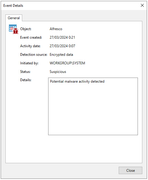
Add me to the list of users who are grumpy with the inline scanning results of 12.1.
I got blasted with many false positives on .onion links with VMs. this thread was pretty helpful in getting me through manually doing some local yara scans which appear show some results, but only false positives that I can find. Of Couse, since the system is online, I couldn't scan all files to be sure. I'm assuming these are false positives given the systems involved, but I've got some comments.
(1) I understand the inline scanning doesn't allow for the most granular level of feedback, but the manual yara scan can give more information, so why can't you at least give some lines before and after the flagged information at the very least? That would be 1000x more helpful than nothing at all. If you can't do it on the backup scan, at least try and implement something like that into the surebackup scan.
(2)Please implement some level of exclusion granularity between scan for everything and exclude from everything. So, I got a false positive on this onion link issue that I want to exclude... my only option now is to exclude that VM indefinitely from all scanning

it would be nice to still monitor that VM for other future warning signs like encrypted files or ransomware notes on that VM even if I exclude it from this specific alert.