I've noticed the following quirks;
- There is no SAML SSO on the VSA console (port 10443). Is it expected that this should only be used for break glass access? I assume that the same for all the JeOS instances (like the JeOS appliances we've deployed as proxies).
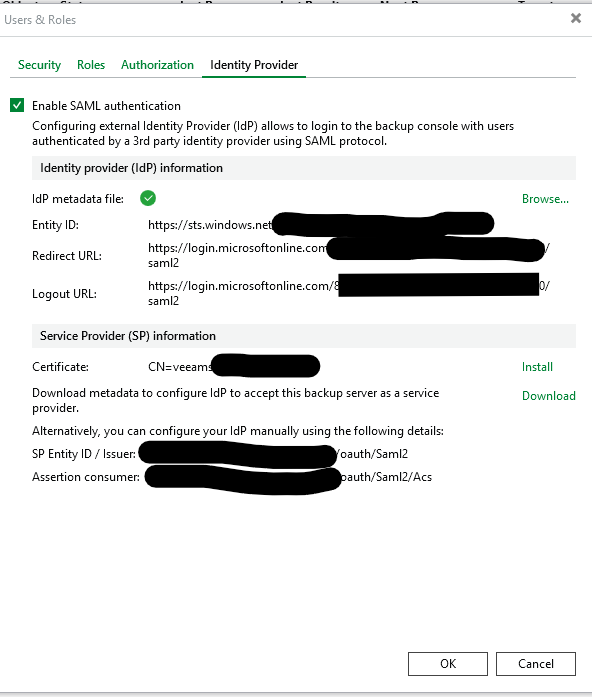
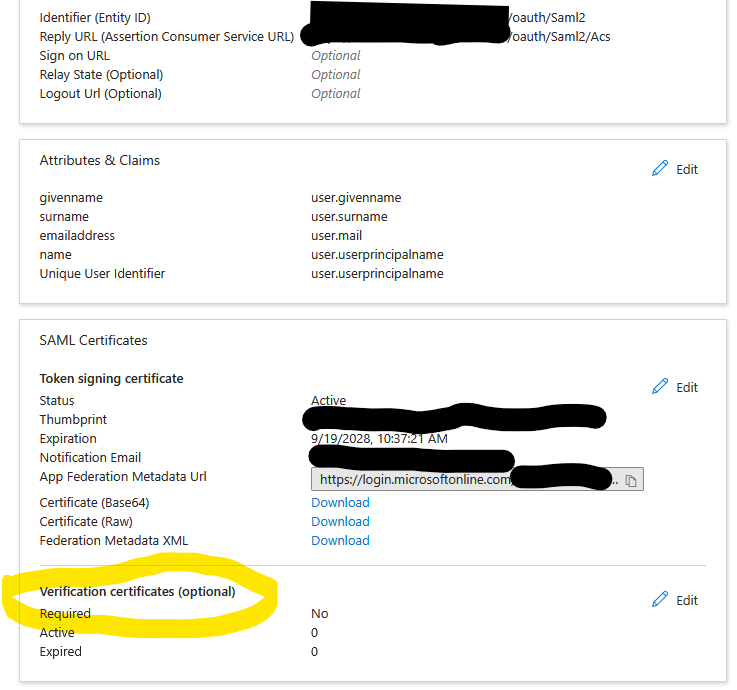
- The SAML configuration with Entra was straight forward, but within the configuration we configured the IdP information via a meta file, but it wouldn't let me move past this screen until I specified a certifcate service provider. I wasn't sure what to do here so the only cert I was able to select was by hitting on the install button and selecting the "select an existing certificate form the certificate store" ,then selecting the cert with he name "Veeam Backup Server Certificate" . Is this correct? Im not sure I understand why this needs to be selected if we aren't using verification certificates in the Entra configuration. - I might be misunderstanding things here though as I don't work with SSO very often.
- Are we able to configure the security officer role to use SAML? Reason why its hard in a large organisation to use local accounts for anything- especially when it requires MFA which generally isn't shared - and especially as everyone is operating within the context of a role rather than as an individual. Perhaps a simple guide for configuring VSA with an Entra app might help noobs like me.
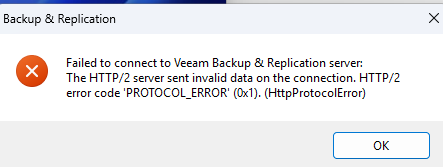
- To make things more straightforward in out environment and to utilise our Lets encrypt architecture, I've reverse proxied the veeamsa appliance as veeamsa.<domain-name> and veeamsa-console.<domainname> with the later going to port 10443. This appears to work fine for the web based clients, but the windows client now fails to connect see image below. I see from our haproxy configuration that we are proxing using the http 1.1 protocol over http2 for backwards compatibility with other sites. Is there a setting on the windows client to use http1.1 instead of http2 otherwise our topology becomes more complex or could this be exposed as a configuration option on the appliance (ie. HTTP Protocol: 1.1 or 2). I don't appear to easily be able to change haproxy as this requires the protocol to be tied to a unique IP (in the haproxy frontend) and I don't have access to any addition IPs without having to beg the security teams for permission. Alterntively How do we progratically change certs so that we can remotely push cert to the appliance and restart the webservices on the appliance to be able to change them when the rest of our cert automation happens about once every 60 days?
- Once SAML was set up though, All I needed to do was to add the user to the the enterprise app, and then also add that user as an "external" user to the Veeam users - easy as.